Cynthia was in the midst of wedding planning, immersed in decisions about venues, flowers, and guest lists, when she received an urgent alert on her phone. The text claimed to be from her bank, warning her that she needed to confirm account details or risk losing access. The message was startlingly detailed, containing her birthdate, full name, and even her bank account number.
Reassured by the legitimacy of the information, Cynthia clicked on the link, which led her to what appeared to be an official bank portal. She entered her login details, received a confirmation message, and, feeling secure, returned to her wedding preparations. However, three days later, she discovered that over $25,000 had been drained from her account.
Cynthia had fallen prey to a sophisticated spear phishing attack.
What is Spear Phishing?
Unlike traditional phishing, which casts a wide net to catch unsuspecting victims, spear phishing zeroes in on specific individuals, using personal information to create a sense of legitimacy. In Cynthia's case, the attacker had gathered enough detailed information to craft a message that seemed entirely authentic.
This wasn't the work of an ordinary scammer. Spear phishing is a precise, targeted attack, often leveraging social engineering — the art of manipulating people into divulging confidential information.
Understanding Social Engineering
Social engineering is a modern term for an age-old tactic: deceiving individuals into revealing sensitive information. What makes these tactics particularly dangerous is their exploitation of human behavior — traits like trust in authority and the tendency to be helpful or act quickly in response to perceived threats. Even in an era of advanced cybersecurity technology, human vulnerability remains the weakest link.
Types of Social Engineering Attacks
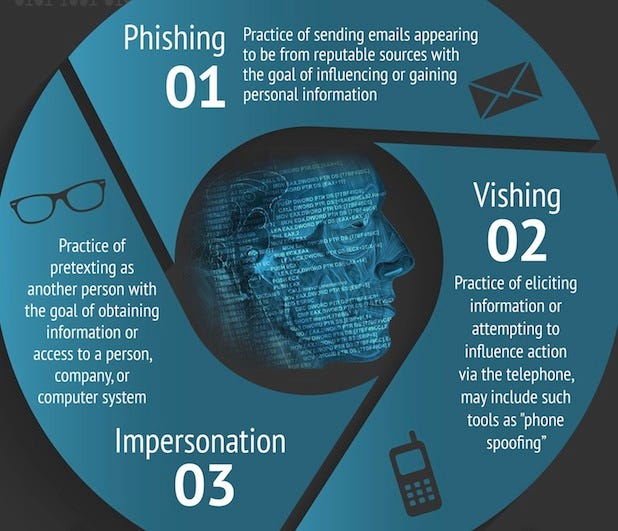
The Anatomy of a Social Engineering Attack
In Cynthia's case, justice was eventually served, but the story reveals the cunning nature of these attacks. The attacker wasn't a random hacker; it was someone close to Cynthia who collaborated with a professional hacker. The insider provided personal information, making the fraudulent message nearly indistinguishable from a legitimate communication.
What's particularly alarming is that these attacks often require minimal technical skill. In Cynthia's case, basic tools were used, but it was the insider's knowledge that transformed a simple scam into a successful breach.
However, hackers don't always need an insider. Data breaches from companies like Ticketmaster and CDK Global have exposed billions of individuals' personal information, providing cybercriminals with a treasure trove of data to exploit.
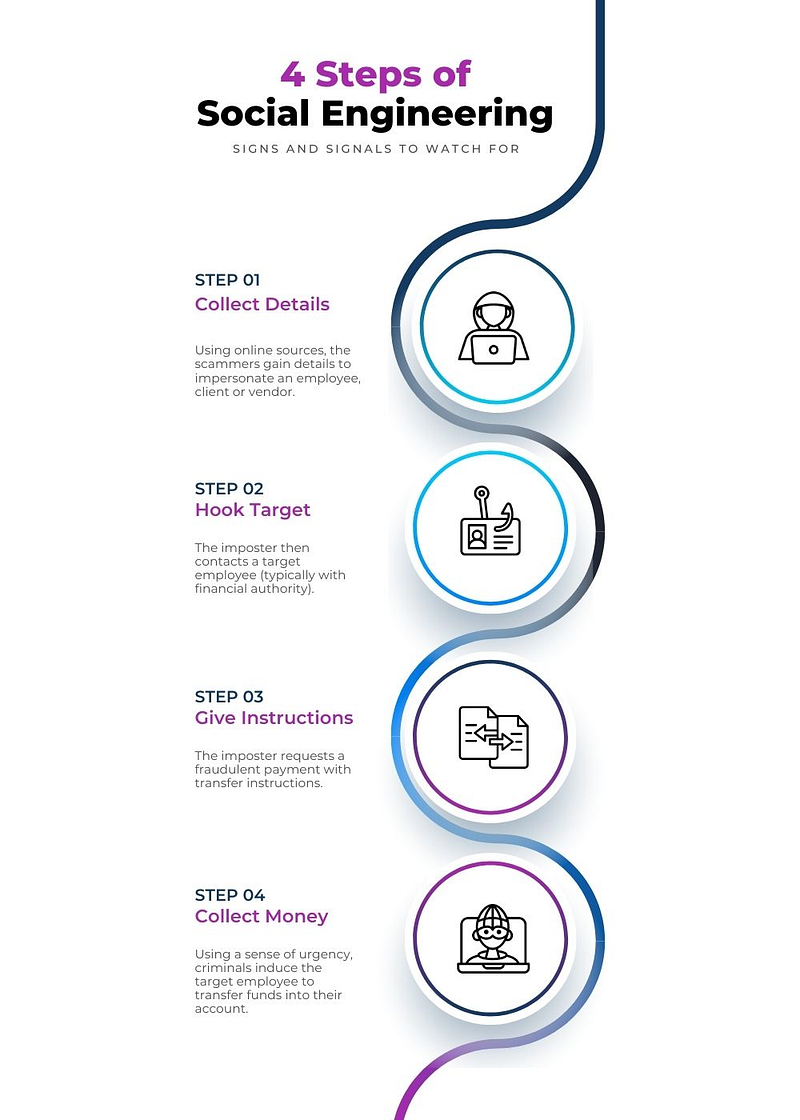
The Typical Steps of a Social Engineering Attack
How Does This Affect You?
Imagine you're a malicious actor with a database of personal information — no financial data, just emails, social media profiles, and some addresses. This data, while seemingly harmless, can be used to extract more valuable information.
For instance, say you discover customer data from a local gym. By examining their social media accounts, you can craft a phishing email that seems to come from the gym, complete with inside jokes and promotions. Victims are likely to click on the link and provide their payment details, thinking they're making a legitimate purchase. Instead, they've handed over their credit card information directly to you.
The gym, unaware of the breach, will soon face a flood of complaints and must quickly engage in damage control. By the time they act, it may be too late — the damage is done.
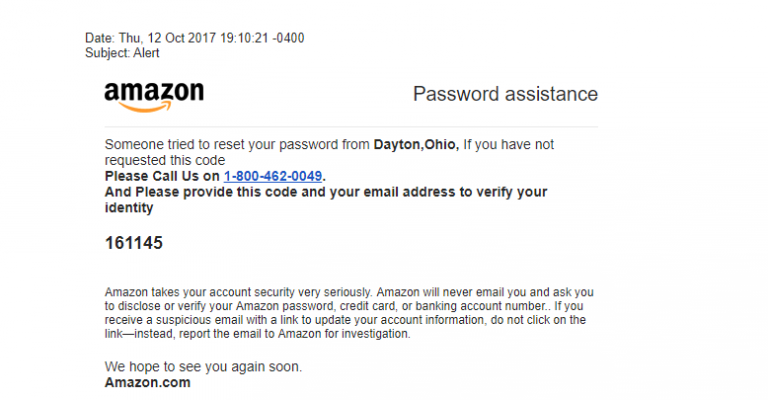
Below is Fake Password Reset to Resemble an Official Amazon Email
How to Protect Yourself
So, how could Cynthia have avoided falling into this trap? Here are some key lessons:
- Verify the Source: Always verify the authenticity of unsolicited messages. Contact your bank or service provider directly using official contact details, rather than relying on the information provided in the message.
- Understand Bank Policies: Familiarize yourself with how your bank communicates with you. Legitimate institutions will never ask for sensitive information via text or email.
- Avoid Clicking Unknown Links: Never click on links from unknown or suspicious sources. On smartphones, this is particularly critical, as they often hold vast amounts of personal data.
- Educate Yourself and Others: Stay informed about the latest social engineering tactics and share this knowledge. Awareness is the first line of defense.
