Disclaimer: I'm not saying WordPress is bad or that you should abandon it if it works for you. However, there are critical security considerations you should be aware of.
One of the biggest aspects of my business is website security. Focusing on small and medium-sized businesses means that most often their website is their key external vulnerability, and for most of them, WordPress is their platform of choice. It offers users enough control to set up a professional-looking website without much technical knowledge.

I've used WordPress countless times throughout my life. It's been a fantastic tool for me, as it has been for many entrepreneurs. Its ease of use and seemingly endless templates empower users to set up beautiful, professional-looking websites without much technical experience. I remember setting up my first websites with it as early as high school, and quite honestly, little has changed since then.
When I started with WordPress, my knowledge of HTML, CSS, and JavaScript was nonexistent. Yet, I could set up highly professional sites quickly. Eventually, I learned to code, unlocking the possibility of manually editing a website, and I left WordPress behind… until recently.
Your Classic WordPress Editor
I turned once again to old reliable when I wanted to set up an early website for Blue Shield. I needed something that would look professional in a short period of time, and WordPress fit the bill perfectly.
I always intended to rebuild my site and move it off the WordPress platform, but time constraints held me back initially. Now, I can thankfully say it's goodbye to WordPress as that process is complete.
Before I parted ways, though, I decided to run some vulnerability tests on my WordPress site. It was through this process that I discovered something alarming: WordPress is far more vulnerable than I had previously thought.
So, What's the Big Deal?
During my scan, I uncovered several significant vulnerabilities that made me rethink using WordPress for any security-sensitive projects.
1. Server-Side Injections
One of the most concerning issues was the susceptibility to Server-Side Injection attacks. These occur when an attacker sends malicious code to be executed on the server hosting your website. This can happen through various input fields, file uploads, or even manipulated HTTP headers.
In WordPress, plugins and themes that aren't securely coded can allow attackers to inject code that the server then executes. This can lead to unauthorized access, data theft, or even complete control over your server.
Example Attack Scenario:
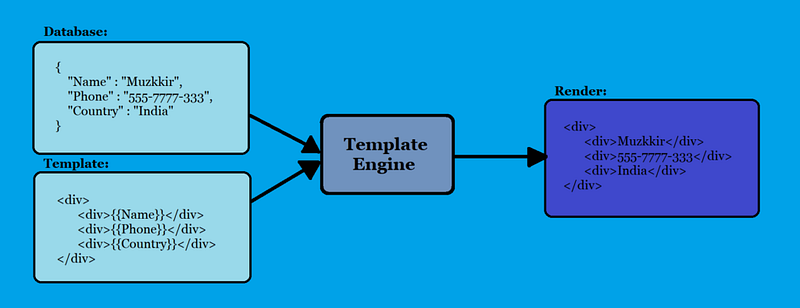
An attacker exploits a vulnerability in a poorly coded plugin to upload a malicious PHP script. Once executed, this script can grant the attacker access to your server, allowing them to steal data, modify content, or use your server for nefarious activities.
How malicious scripts can be injected in to templates to yield data
2. Content Security Policy (CSP) Tokens
Another significant vulnerability I discovered was related to Content Security Policy (CSP) tokens. A CSP is a security standard that helps prevent Cross-Site Scripting (XSS), clickjacking, and other code injection attacks by specifying which dynamic resources are allowed to load.
In my scan, I found that my WordPress site either lacked a proper CSP or had misconfigured CSP tokens. Without a robust CSP, attackers can inject malicious scripts into your site, which browsers will unwittingly execute.
Why This Matters:
A missing or weak CSP allows attackers to perform XSS attacks more easily, potentially compromising user data, hijacking sessions, or spreading malware to your site's visitors.
3. Cross-Site Scripting (XSS) Attacks
WordPress's framework can be vulnerable to Cross-Site Scripting (XSS) attacks, especially when using themes or plugins that haven't been properly secured. XSS attacks occur when an attacker injects malicious scripts into content that is then served to other users.
Real-World Impact:
An attacker could inject a script that records keystrokes, capturing sensitive information like login credentials from your site's users. This not only endangers your users but also damages your site's reputation.
4. SQL Injection Attacks
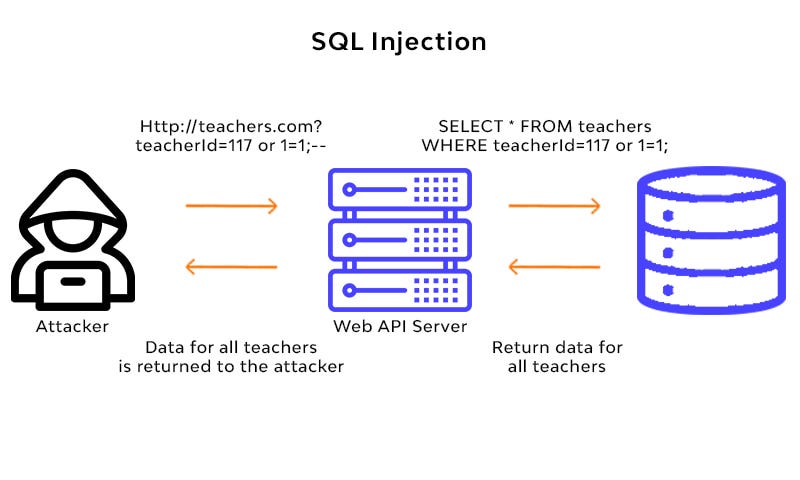
Perhaps the most significant vulnerability is the risk of SQL Injection attacks. SQL is used to interact with databases, and malicious actors can exploit poorly secured inputs to manipulate your database.
Attack Vector:
By injecting SQL commands into input fields like comment sections or search bars, attackers can access sensitive data, alter your database, or even gain administrative control over your site.
Tell-Tale Signs:
If you've ever seen a comments section filled with odd code snippets or gibberish, it's possible that was an attempted SQL injection.
Diagram of an SQL Injection
Other Notable Vulnerabilities
While these were the most significant issues I discovered, there are several other vulnerabilities worth mentioning:
- Outdated Plugins and Themes: Always update your plugins. Using outdated or unsupported plugins and themes can introduce security risks due to unpatched vulnerabilities.
- Brute Force Attacks: Automated scripts can attempt thousands of login combinations to guess your credentials.
- File Inclusion Exploits: Vulnerabilities that allow attackers to load remote files and execute code on your server.
- Directory Traversal: Improperly secured directories can enable attackers to access sensitive files outside the webroot.
- Denial of Service (DoS) Attacks: Overwhelming your server with traffic to cause downtime.
Protecting Your WordPress Site
I want to stress again that if you have a WordPress site, don't panic. There are proactive steps you can take to enhance your site's security. WordPress's widespread use—powering approximately 43% of all websites—makes it a tempting target for hackers, and thus in a way, a victim of its own success. A little awareness and action can mitigate many risks.
Below, I'll outline how you can address the major vulnerabilities highlighted.

Mitigating Server-Side Injections
- Validate and Sanitize User Input: Ensure all forms and input fields validate and sanitize data before processing. Use WordPress's built-in functions like
sanitize_text_field()andesc_url()to clean user input. - Use Security Plugins: Implement security plugins like Wordfence or Sucuri that can detect and block malicious activities.
- Disable File Editing: Add
define('DISALLOW_FILE_EDIT', true);to yourwp-config.phpfile to prevent execution of unauthorized code through the WordPress editor.
Implementing Strong Content Security Policies (CSP)
- Set Up a CSP Header: Configure your server to include a strict CSP header. This tells browsers which content sources are trusted.
- Use Plugins Wisely: Choose plugins that are compatible with CSP and avoid those that require inline scripts or styles, which can weaken your CSP.
- Test Your CSP: Use tools like Google's CSP Evaluator to test your policy for weaknesses.
Preventing Cross-Site Scripting (XSS) Attacks
- Sanitize Output: Use functions like
wp_kses_post()when outputting user-generated content to ensure it's free from malicious code. - Limit Use of Plugins: Reduce your site's attack surface by only using essential, reputable plugins. Plugin bloat also reduces your site's performance, so it is best to avoid it.
- HTTP Security Headers: Implement headers like
X-XSS-ProtectionandX-Content-Type-Optionsto add extra layers of security.
Guarding Against SQL Injection Attacks
- Use Prepared Statements: When querying the database, use prepared statements with parameterized queries to prevent SQL injection. WordPress's
$wpdbclass supports this.$wpdb->prepare( "SELECT * FROM $wpdb->users WHERE user_login = %s", $user_login ); - Restrict Database Permissions: Limit your database user's permissions to only what's necessary for your site to function.
- Monitor and Log Database Activity: Use tools or plugins that can monitor database queries and alert you to suspicious activity.
Addressing Other Vulnerabilities
- Limit Login Attempts: Use plugins like Login LockDown to limit the number of login attempts from a single IP address.
- Secure Hosting Environment: Choose a hosting provider that prioritizes security and offers features like Web Application Firewalls (WAF).
- Regular Backups: Implement regular, automated backups using plugins like UpdraftPlus. Store backups offsite for recovery in case of a breach.
- SSL/TLS Encryption: Install an SSL certificate to encrypt data transmission between your site and its visitors. Services like Let's Encrypt offer free SSL certificates.
- File Permissions: Set appropriate file permissions on your server (e.g.,
755for directories,644for files) to prevent unauthorized access.
Conclusion
While WordPress is a powerful and convenient platform for many, if you're in the cybersecurity business or running a venture that handles a significant amount of sensitive customer data, I can't wholeheartedly recommend it for your site. The potential vulnerabilities and the constant need for vigilant security practices make it less suitable for businesses where security is paramount.
It's essential to weigh the convenience and flexibility of WordPress against the potential risks. For some, the benefits may outweigh the drawbacks, especially if rigorous security measures are diligently implemented. However, for those who require a higher degree of security assurance, alternative solutions—such as custom-built websites using security-focused frameworks like Django with its robust security features—which is what I ended up opting for.
In the ever-evolving landscape of cybersecurity threats, choosing a platform that aligns with your security needs is crucial. Whether you stick with WordPress or opt for a different solution, staying informed, proactive, and vigilant is the key to keeping your digital assets safe.
